Empowering communities through innovation, education, and sustainability.
Learn More Get Started
The world has become a global village due to technology. This advancements in technology across the globe has changed how health, security, education and business matters are handled. The innovations have improved literacy, enhanced skills and catalyzed human co-existence. Yet, in most part of Kenya especially Kitale, most women and youths remain trapped in darkness, poverty and desperation, despite most of them completing their O-level education with promising grades.
The root cause is clear: lack of practical skills for sustainability. While the Kenyan government advocates for full transition from primary schools to secondary education, support for post-secondary skills development is limited to a few. Consequently, many youths resort to risky behaviors, while unskilled women migrate to urban areas seeking work and face exploitation. They find themselves into this not out of choice but circumstances.
At Cotech, we belive all is not lost. By identifying and equipping these women and youths with relevant skills, we open their minds to new opportunities and sustainable livelihoods. Our programs leverage ICT training, tailoring, and fashion design to empower participants, lighting a path to economic independence and community contribution.
Empowering communities through technology, innovation, and sustainable development — enabling youth and women to thrive in a digital, inclusive future.
A connected and innovative Africa where every individual leverages technology to create solutions, opportunities, and lasting impact.
Promote digital literacy among youth and women. Encourage innovation and community-driven solutions. Support sustainable technology-based livelihoods. Bridge the digital divide through education and mentorship.

Learn web, mobile, and software skills for career growth.
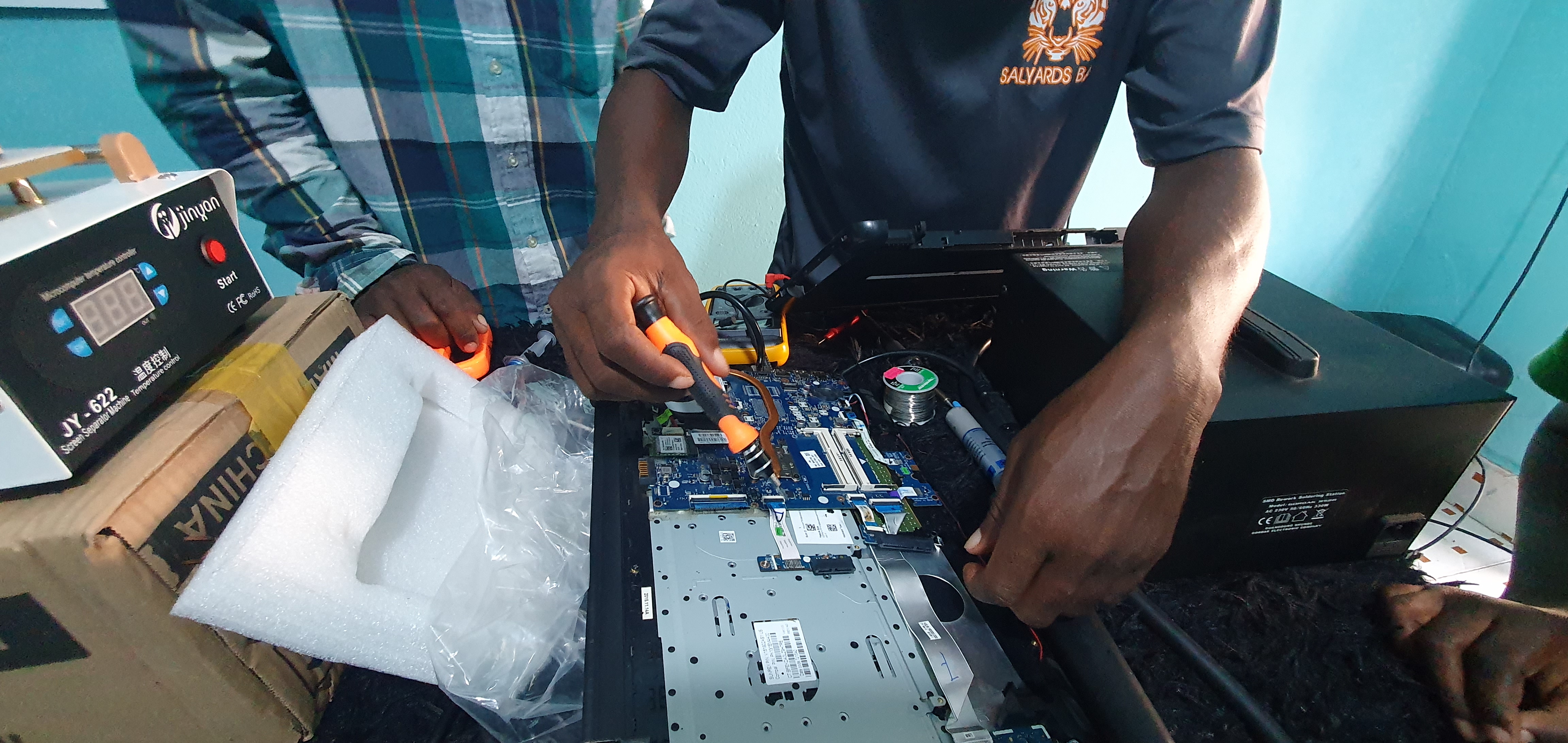
Empowering youth with ICT skills in repair and maintenance to meet growing digital demands.

Sparking children's interest in technology through coding and creative activities.

Climate-smart organic farm fostering innovation, education, and sustainability.

Hands-on training in carpentry, joinery, and furniture making for youth empowerment.

Practical skills in fashion design, dressmaking, and textile management.
Through a holistic approach, Cotech continues to empower communities and transform live
In continued advocacy for quality training, unified approaches, and sustainability, our Founder, Mr. Josphat, will chair the ICT Curriculum Committee in Nairobi, sponsored by Connection Ubuntu.
Cotech launches a recruitment drive to empower women and youth through skills training.
Mary used Cotech ICT and Tailoring training to start her own business, employing 5 women and supporting her family sustainably.
John leveraged his skills from Cotech's TechKnow Kids program and smart agriculture training to grow a profitable agro-business.


